Validian Corp. (VLDI:OTCQB) is uniquely poised to protect major investments in the automotive sector that are one hack away from enormous liability. Just this week, Uber announced its intent to do a $10 billion deal with SoftBank, a Japanese conglomerate. It's pretty clear that the automotive market represents the "new screen" advertisers are jockeying for position. Despite the massive capital inflows, there are no credible solutions that are capable of protecting the automobiles we are driving right now against any of the recent global cyberattacks.
Successful attacks like the WannaCry ransomware and the Saber Travel Reservations breach demonstrate how poorly prepared the market is for future occurrences. Since nothing has been fixed since the breaches earlier this year, hackers would use the same methodology to attack vehicles. Using the same combinations of crypto protocols such as TLS, PKI and/or PGP plus filters such as smart firewalls, intrusion and threat detection and prevention haven't paid off too well and estimates by Cyber Security Ventures put the cyber damage at $3 trillion in 2015, with it projected to grow to $6 trillion by 2021. Therein lies the opportunity for exponential growth of new cybersecurity approaches that actually solve the cyber risks in the automotive market segment because nothing has been adopted yet.
Major Players Moving into Automotive Connectivity
In 2014, Apple (APPL) began "Project Titan" and assembled up to 1000 employees to work on developing an electric vehicle at a secret location near its Cupertino headquarters. AAPL eventually shelved the project but then used its resources to create an autonomous driving system that would eventually partner with existing car makers with the idea of deeply integrating the iOS devices. CEO Tim Cook stated "we're focusing on autonomous systems. It's a core technology that we view as very important. We sort of see it as the mother of all AI projects. It's probably one of the most difficult AI projects actually to work on." Early in 2017, AAPL was granted a permit from the California DMV to test self-driving vehicles on public roads. This is one of 54 permits granted by the California DMV, which includes the usual suspects like all the major auto manufacturers including Tesla (TSLA), but other names like Nvidia (NVDA) Baidu (BIDU), Waymo (GOOG) and Telenav (TNAV) are a few notable mentions.
Waymo, which is part of Google, is the leader in autonomous drive and since 2015 has racked up an impressive 1,031,199 miles of autonomous driving based on the yearly disengagement reports required as of 2015. Disengagements are incidents when the backup driver takes control of the car for safety purposes. When Waymo started in 2015, the ratio of disengagements per 1000 miles was 0.8 and that plummeted to 0.2 in 2016, indicating a trend toward greater reliability. Uber seems to be riding on the coattails of Waymo, which is suing Uber for IP that Anthony Levandowski brought over from Waymo. Uber has about 400 people located in Pittsburg, Pennsylvania, working on the autonomous car. Most of its talent came from Carnigie Mellon's robotics program. When measuring the program's success by disengagement, Waymo still has the commanding lead. Uber had only 20,354 autonomous miles as of March 2017 compared to Waymo's 1 million plus.
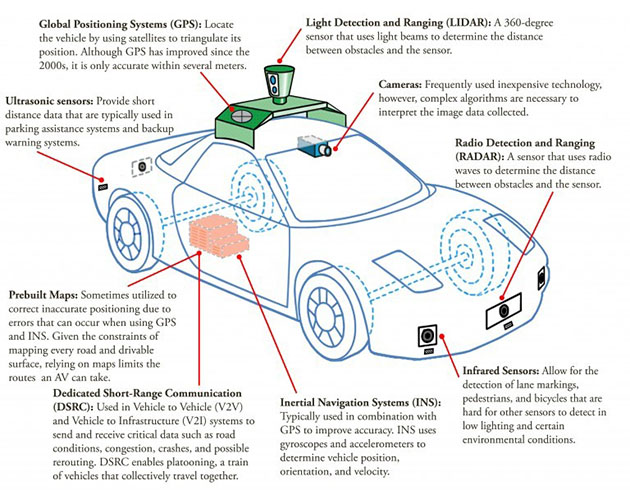
University of Michigan Fact Sheet
In March 2017, Tencent Holdings (TCEHY) made a 5% open market purchase and bought 8,167,544 shares of Tesla (TSLA) for about $1.778 billion. This made it one of Tesla's largest shareholders. Tencent is a Chinese technology holding company with a diverse portfolio of tech investments. Among its holdings are WeChat, Moments and Mobile QQ. In the gaming world, it owns a controlling interest in Riot Games and Supercell. Baidu (BIDU) and Alibaba (BABA) are also major players in the automotive connectivity space and Tencent is using this investment as an opportunity to get exposure to this burgeoning market to compete with its counterparts BIDU and BABA.
BABA unveiled its smart car in July 2016 and with the three LED screens and four detachable 360 degree cameras, it's pretty clear that this is a car that is connected to the internet. BIDU followed suit mid-2017 with its launch of Apollo, which open sourced the AI of the self-driving car. Big money seems to really like this sector.
Disruption Increasing the Pace of Innovation
There appears to be a lot of debate surrounding the autonomous market and what it will look like but the digitization is exploding right now. The car has become the new screen and a booming platform for passengers to consume media. Advertisers want in. Cars are getting more and more complex with massive wiring harnesses and sensors. The average vehicle contains over a mile of cabling weighing approximately 50 pounds. Smart cars contain 60–100 sensors and expect to reach as high as 200 by 2020. Electric cars contain three times the amount of cabling and sensors in a smart car, so it not hard to see how this group alone is increasing the pace of innovation.
Digitization involves the evolution of connecting the vehicle to the internet. Right now, there are simple things like GPS maps, content streaming and hands-free mobile phone operation. The future will connect the car to the supply chain and notify the driver when parts are ready to fail. The IoT sensors may create a mesh of data giving real time weather monitoring.
Increasing Automation. The autonomous car will replace drivers doing ridesharing or on long truck routes. The automation will happen in stages and has already begun as riders enjoy blind-spot monitoring and automatic braking.
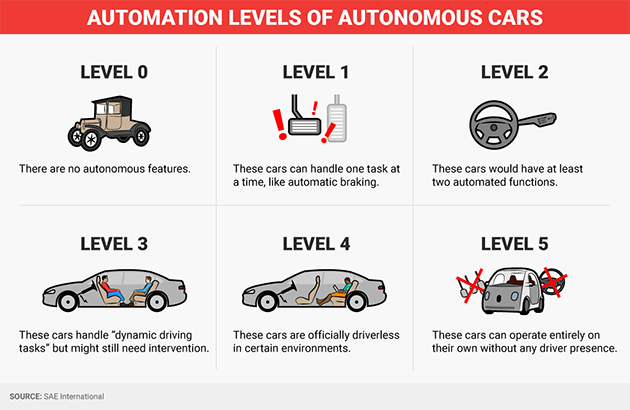
Shared Mobility. Car growth is slowing due to e-hailing apps like Uber, Lyft and new car pooling apps. Estimates show that 1 out of every 10 cars is a shared vehicle. There used to be a time when getting a driver's license was a big deal. Due to the disruption of e-hailing services, the share of young adults (16-24 years old) obtaining a driver's license dropped from 76% in 2000 to 71% in 2013 against a backdrop of over 30% in the car sharing market in North America over the past five years. The ride sharing and car hailing apps will morph into Mobility as a Service (MaaS).
Things That Can Go Wrong: What's at Stake.
If cars get hacked, then people can die. Car hacking is no longer something you see in spy movies but a real, identifiable threat that needs to be treated seriously. In 2014, WikiLeaks released the Washington Post documents that the CIA was looking into hacking cars to carry out "nearly undetectable assassinations." In 2015, a reporter, Charlie Miller, and hacker, Chris Valasek, rode in a 2014 Jeep Cherokee that was hacked by shutting down the engine and disabling the brakes. In an email after the hack, Valasek said "it doesn't appear that any manufacturers currently have detection/prevention methods for such attacks." This hack prompted the recall of 1.4 million vehicles. Terrorists intent on causing chaos could target self-driving cars by turning the wheels of the car, or pushing the accelerator or even braking. Sending a false signal to the GPS could cause the vehicle to go off its route and crash. The automotive sector is at great risk of attack and the recent examples highlight how vulnerable cars really are. All the buzz is talking about driverless cars but the immediate threats are to cars on the road now.
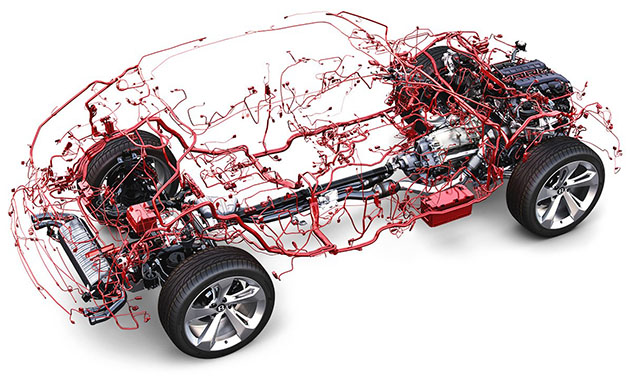
Bentley Bentayga's Wiring Harness with 90 computers interconnected = Target Rich Environment
Current Problem: Cybersecurity Not Equipped with the Correct Tools
Cybersecurity players like Palo Alto Network (PANW) and Oracle (ORCL) use a combination of smart firewalls, intrusion detection and prevention systems, and monitoring. These are bulky, data intensive and bandwidth intensive programs that can only go after KNOWN THREATS. While they may have a role, it has become obvious that they are not a standalone solution for any implementation, let alone automotive systems. It is just as obvious that the use of end-to-end encryption for data transfer and separate encryption for storage is not working either. There are so many ways in—that bypass filters and crypto protocols. All the successful cyberattacks would use the same means to attack automobiles.
And there are other cyber exposures for automobiles. Bluetooth is almost a standard item in a newer car these days. The key issue is that Bluetooth can be hacked to access mobile devices, computer systems and the data, AND all modern cars and vehicles have Bluetooth, AND also because of the increasing severity of distracted driving laws, more and more drivers are also using Bluetooth to talk on their smartphones. Cars have specially designed docking ports to allow access to the smartphone or other mobile device encouraging their use.
It's hard to comprehend but the tire pressure monitoring systems (TPMS) is an IoT device that can be tracked or hacked to disable the car or put it into a limp home mode. Researchers have speculated that the TPMS chip could trigger an explosion. Event Data Recorders are like black boxes for vehicles and they can be hacked too, allowing you to replace guilty evidence for the insurance company.
Unveiling the Solution
The ideal solution would have to break the mold of traditional cybersecurity and be radically different and innovative. The automobile manufacturers would need a security protocol that is very streamlined and that could not only secure the computer at the point of entry but also secure the IoT sensors in the vehicle. Since sensors don't have much memory, the software would need to be compact and be no more than 1.5 MB and for some IoT less than 1 MB. Given all the devices that currently exist it would need to be a software overlay or integration rather than a chip or hardware based solution. The software would need to be easy to implement and be able to control the permissions upon which users could access. It would also need to work with various protocols like Bluetooth, satellite and cellular and still operate in a compromised environment.
Although it has taken over 10 years of development and $50 million in R&D, a solution does exist called Validian Protect, which was born out of the need to fix the gaping security holes in the Bluetooth protocol. Validian Protect is a rapidly integrated middleware that works on any operating system and technology platform so it is ideally suited for automotive connectivity, which may use different operating systems including Android, Apple iOS and QNX and technology platforms like mobile and IoT as well as hosting servers. When pitching a new cybersecurity software to the automotive market the very first objection will likely be about compatibility. Validian's solution is ubiquitous and works on all platforms.
Validian Protect seamlessly protects the transfer, storage and usage of data. Additionally, it protects the applications and devices against network-borne vulnerabilities such as intrusion, impersonation and interception and against host-borne vulnerabilities such as memory-scanning and file system scanning. These features would make the automobile immune to cyberattacks. Another feature more relevant to the instant messaging market than the automotive market is that this software can provide flexible control over usage and retraction of data and immediate alerts on the usage or attempted misuse of data. The government with all its top-secret projects would love this feature since it would allow them to cut their internal monitoring budget to the bone.
This software protection encompasses the devices that control the vehicle's function, the IoT sensors within the vehicle, and the applications running off the sensors. Essentially anything hooked to the brains of the car's computer would be covered down to the phone sitting in the cradle of the dashboard. In this closed realm, the vehicle is impervious to cyber-attack. This means that any type of known or unknown cyber-attack or vulnerability or if any other devices or networks have been hacked or improperly accessed, infected with viruses or malware, or otherwise compromised it would still be protected. In reality not even a fully hacked phone plugged into the cars computer could disrupt the operation of the vehicle.
This is a radically different approach versus all other cybersecurity approaches, which are a combination of individual point solutions comprising crypto protocols and filters, each targeting a different cyber exposure, but do not work seamlessly together wherein hackers can easily exploit the gaps between them. What all these other cybersecurity solutions are missing is the core assumption of Validian Protect. Every device is compromised. This software operates in a realm that assumes the device is infected yet still allows for the transport and manipulation of data.
This could be the magic bullet for the automotive market and with the right partner could see industry wide acceptance. Typical proof of concept trials take 2-4 weeks to implement with Validian Protect, so investors should keep watch for any VLDI licensing agreements with major automotive manufacturers or other large proponents of auto connectivity.
INVESTMENT CONCLUSIONS
1. Cybersecurity Protocols for Automobiles—Adopt VLDI / Create from Scratch
Major investments in automotive connectivity have arrived with hundreds of billions of investment dollars at risk and the stakeholders are looking for solutions. The missing component seems to be cybersecurity. Negligible security exists today, so stakeholders are not boxed into keeping entrenched solutions that don't work despite pouring billions of dollars into them. The automotive thought leaders may simply choose to adopt Validian's simple to implement, cookie cutter security module or look to develop their own from scratch which would take a number of years and likely cost double what VLDI has already spent in the way of development. Adoption seems to be inevitable.
2. Undervalued on Multiple Accounts—Hedge Against Hacking Loss
Regardless of what the automotive market does there are other sectors even larger than automotive such as mobile messaging and social media that could use these cybersecurity solutions. With approximately 650 million shares outstanding on a fully diluted basis and a market capitalization under $4.5 million, investors should understand the great divide between the current market cap and what one of these big investors would be willing pay to protect their billions of investment dollars. Everything the automotive connectivity investors are building is worthless without a cybersecurity solution. This is a must have item for them and no one else has a solution. With a two to four week implementation time for test results, what players wouldn't look at this as an insurance policy? In VLDI's last press release it mentioned being ideal for auto connectivity. For the company to say that it must be meeting at the CTO level or higher. It's not hard to speculate that a deal might be brewing and the size of the players it is likely engaging with could translate to some very large numbers.
Market Cap is Too Low with Respect to Earnings Potential
To understand the true value of the stock, investors need to put themselves in the shoes of the big investors like Uber who have $10 billion at risk. VLDI could be viewed as an insurance policy with the big question of what would the investors be willing to pay for insurance? If investors find out that Validian Protect works as advertised and stops 100% of the threats, then is $4.5 million or the entire market cap of the company all they would pay to protect $100 billion or could it be multiples of that? By the most traditional valuation models, a company's IP should be valued at multiples of cost, which is $50 million or roughly $0.08/share, which also corresponds to the last large level of financing completed. The market has undervalued this revenue model with tens of millions of earnings potential. Investors can wait for the sales to come in and pay a premium price or start buying in anticipation. Connect the dots—revenue is on its way.
Michael Sheikh is the founder of Falcon Strategic Research, which focuses on small-cap and micro-cap companies that are not covered by traditional analysts on Wall Street. Sheikh is an Air Force Academy graduate with a degree in economics; he was a KC-135 pilot. He was a stock broker for Dean Witter and was a research analyst for National Securities, covering the aerospace sector. He is a contract CFO for various public companies.
Want to read more Streetwise Reports articles like this? Sign up for our free e-newsletter, and you'll learn when new articles have been published. To see a list of recent articles and interviews with industry analysts and commentators, visit our Streetwise Interviews page.
Disclosure:
1) Michael Sheikh: I, or members of my immediate household or family, own shares of the following companies mentioned in this article: Validian. I personally am, or members of my immediate household or family are, paid by the following companies mentioned in this article: None. My company currently has a financial relationship with the following companies mentioned in this article: None. I determined which companies would be included in this article based on my research and understanding of the sector.
2) The following companies mentioned in this article are sponsors of Streetwise Reports: None. Streetwise Reports does not accept stock in exchange for its services. Click here for important disclosures about sponsor fees. The information provided above is for informational purposes only and is not a recommendation to buy or sell any security.
3) Statements and opinions expressed are the opinions of the author and not of Streetwise Reports or its officers. The author is wholly responsible for the validity of the statements. The author was not paid by Streetwise Reports for this article. Streetwise Reports was not paid by the author to publish or syndicate this article.
4) This article does not constitute investment advice. Each reader is encouraged to consult with his or her individual financial professional and any action a reader takes as a result of information presented here is his or her own responsibility. By opening this page, each reader accepts and agrees to Streetwise Reports' terms of use and full legal disclaimer. This article is not a solicitation for investment. Streetwise Reports does not render general or specific investment advice and the information on Streetwise Reports should not be considered a recommendation to buy or sell any security. Streetwise Reports does not endorse or recommend the business, products, services or securities of any company mentioned on Streetwise Reports.
5) From time to time, Streetwise Reports LLC and its directors, officers, employees or members of their families, as well as persons interviewed for articles and interviews on the site, may have a long or short position in securities mentioned. Directors, officers, employees or members of their immediate families are prohibited from making purchases and/or sales of those securities in the open market or otherwise from the time of the interview or the decision to write an article, until one week after the publication of the interview or article.
Graphics provided by the author.